6 Steps to Check WordPress for Malware

With over a quarter of all Internet sites running on WordPress, it’s a common target for malware scripts and hackers. Mix in thousands of open source plugins and themes (some coded better than others), poor shared hosting practices and weak password management, and you have the perfect recipe for an insecure site.
Here are six steps to check your WordPress site for a malware infection. These are ordered from easiest to hardest.
1) Online Malware Scanner. For a free, quick and easy check, you can’t beat Sucuri’s Malware and Security Scanner. Just enter the URL of your site and you’ll get an online report of your site’s status along with a blacklist report. There’s a little upsell of their Website Firewall product (the “Medium Risk” you’ll see) but otherwise this is a great tool for a quick check.
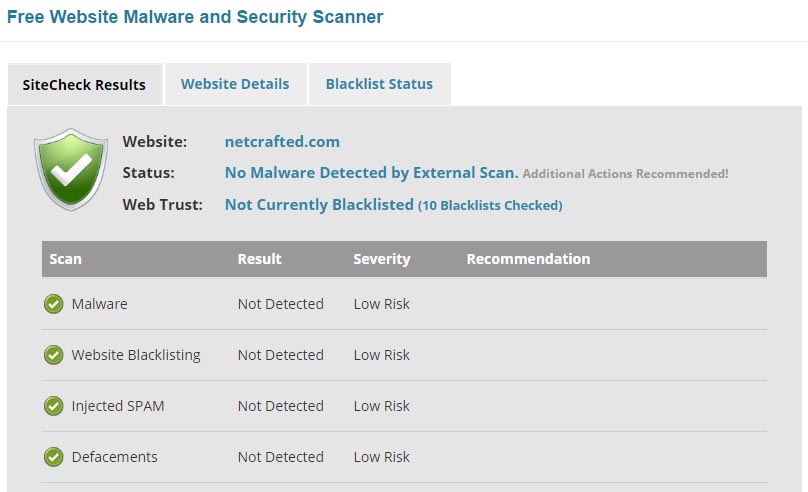
2) Check the Search Engines. An infection that’s been lingering for a while is likely to have already been picked up by one or more of the big three search engines: Google, Yahoo and Bing. The search engines will display a warning to users that your site is infected and dangerous to visit.
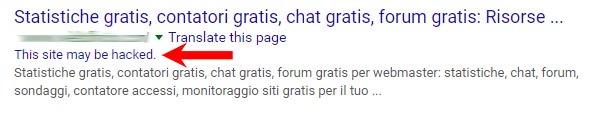
You can perform a site specific search by using the site operator. Simply prepend the operator site: before your domain name. For example, I could check my site with site: netcrafted.com. Check for a message below one or more of your search listings. While you’re looking for the message, take a look at the content that’s been indexed; if you see unusual characters or content that clearly doesn’t belong, it’s a good sign you have an infection.
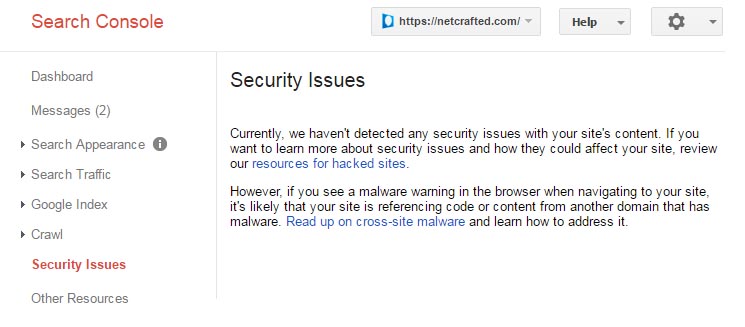
3) Google Search Console. If your site isn’t setup in Google’s Search Console, it should be. Not only will you will be able to check the malware status of your site, it also helps you monitor and maintain your site’s presence in Google Search results. It’s completely free and a no-brainer for any serious website owner.
Once logged into Search Console, you’ll find the status of your site under Security Issues. If there are notices here, you likely have issues. After you fix them, this is where you’ll return to in order to submit your site to Google for reconsideration.
4) Scan with Wordfence. The Wordfence Security plugin is one of my favorite security plugins. I use Wordfence as a basic line of defense on my own site and sites I manage for others.
Before you run a scan, go to the Scans to Include options section and check every checkbox except for the ‘Scan images, binary, and other files’, ‘Enable High Sensitivity’ and ‘Use low resource scanning’ options.
Keep in mind that relying solely on an internal scanner on an already compromised site is foolish; however, if Wordfence does find malware it’s a sign you have much bigger problems.
5) Visit from search, social media & mobile. Some malware infections are designed to only show themselves when being referred to your site from another source. For example, visiting from Google or Facebook. The possibilities are vast, but I find it most useful to test the most popular search engines and social media platforms.
Before you start, I recommend loading a new browser window that isn’t logged into your site. Clear all cookies and your browser’s cache. Chrome’s Incognito mode is especially useful for this testing.
For search engines, do a site specific search using the site: operator just as before. Click on a link to your site. If anything appears abnormal, there may be a problem.
Do the same for Facebook, Twitter, Instagram or any other social media platform you might find your site linked from.
The key here is to click to your site from another site. The web server hosting your site will receive the refering URL information and this is what some malware infections use to determine whether or not to “show” themselves.
Finally, load your site in mobile and check it. With mobile browser usage on the rise, malware authors are now selectively targeting these views.
6) Examine your files. This is the going to be the hardest way to inspect your site, but if you know what you’re doing, you can spot active and inactive infections. Your host’s file manager is usually the easiest way to do this, but an FTP client will also work.
Look for unusually named files and inspect the contents of some commonly infected files. Malware code is often found in files such as .htaccess, index.php and wp-config.php. Compare your core WordPress file list to those found in the original release package. If you have shell access to your host, you can grep for commonly used functions in malware such as eval(base64_decode.
What Next?
If your site is clean, now’s a good time to make sure it stays that way. Harden WordPress, keep it up to date and have a sound backup plan in place. Consider WordPress management or managed WordPress hosting if you want to offload these worries.
An infected site should be cleaned as soon as possible. Refer to my step-by-step guide on how to remove a WordPress malware infection or consider my professional WordPress malware removal service.
